
Can You Spot a Hidden Fraud Attack?
No two fraud attacks are created equal. Some massive attacks appear seemingly out of nowhere, while others have a clear build-up. Some are obvious, some are stealthier, and some aren’t really attacks at all.
All of this is by design. Fraudsters want to keep fraud teams guessing and often use a combination of tools and strategies to misdirect them. But just like night-vision goggles help us see in the dark, there are ways to spot an attack that is hiding in plain sight.
Let’s look at a couple of examples. See if you can tell where these attacks are hiding, and if you can see through fraudsters’ battle plans.
The Brute-Force Blitz
When investigating a large, short-lived attack, we’re on the lookout for a massive fraud spike that quickly appears and disappears in a matter of hours or days (though there’s more to it than that, which I’ll get to in a moment).
Look at the graph below, which shows the total volume for a credit issuer over 90 days. This is the visibility that most businesses have — they can see peaks and valleys in total traffic but have no way of knowing in real-time which spikes are good, and which (if any) are worrisome.
Imagine you’re the head of fraud for this business, and your team knows there’s been an influx of fraudulent users infiltrating your application — you just don’t know when, where, or how it happened. I’ll let you know that the attack lies in one of these traffic spikes, but it’s up to you to figure out which one to investigate:
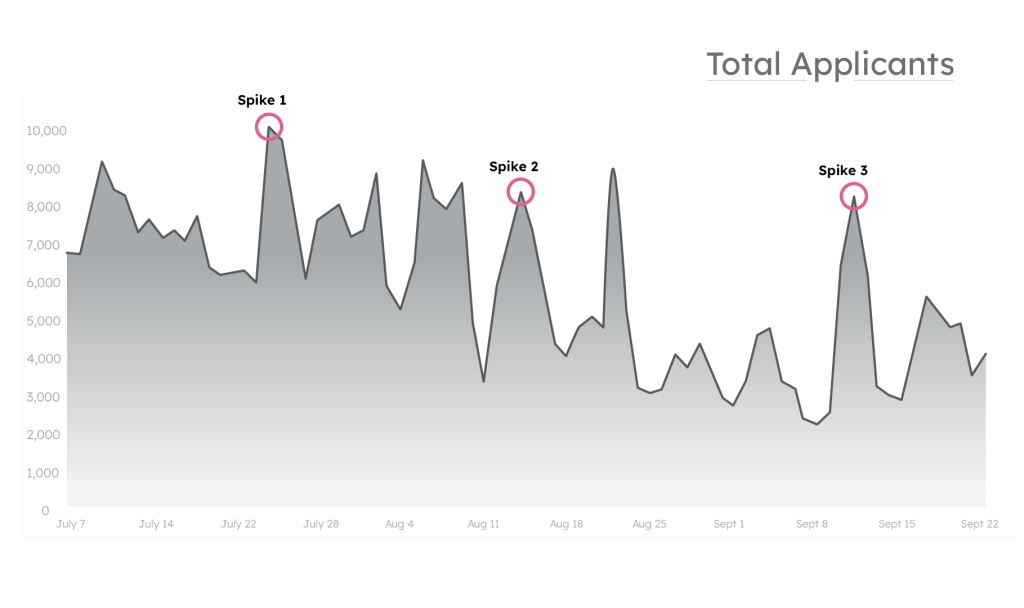
Which spike contains a fraud attack?
You found the peak of the attack, but let’s back up a bit to see if we missed anything leading up to it. Now, we’ll analyze this attack through the lens of behavioral analytics, which can segment genuine from risky traffic in real time, and tell us what type of attack (human- or bot-led) we’re facing. Breaking down the human and bot traffic preceding this attack reveals something interesting:
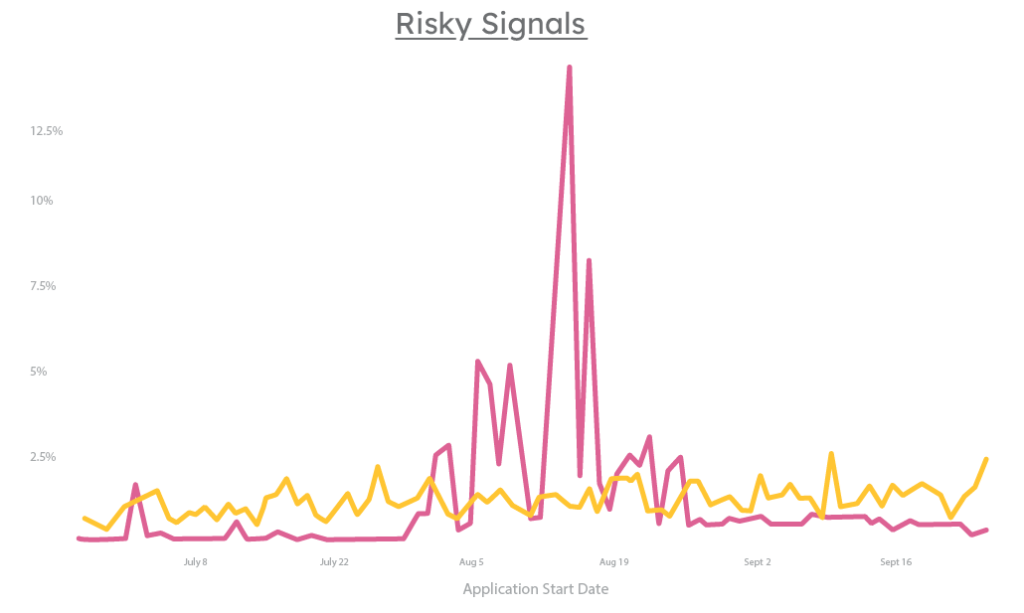
Ahead of the bot attack, humans (yellow) and bots (red) alternate smaller spikes. We see this enough to know exactly what it is: human fraudsters are probing the credit issuer’s controls for weaknesses, then testing bot scripts to exploit what they found. They fine-tune their scripts over multiple iterations, until they land on one that’s attack-ready. With behavioral analytics, you could’ve seen this pattern building and stopped the attack before it happened.
The Attack Within the Attack
This graph shows the total traffic for an online lender. I’ll go ahead and share the risky (red) vs. Genuine (green) breakdown now, because we can all tell where the anomaly is.
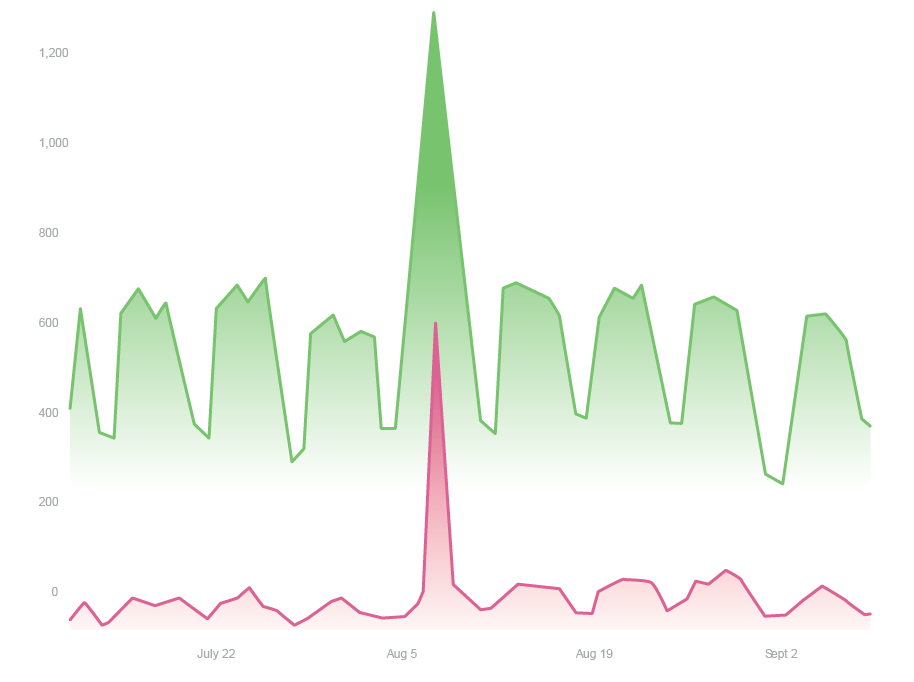
It seems obvious where the attack is happening — the big red spike in the middle is impossible to miss. But when we put on our night vision goggles and segment human fraud from bots, we see something that was completely masked by what appeared to be normal traffic patterns. Here’s what’s lurking under the surface of each spike:
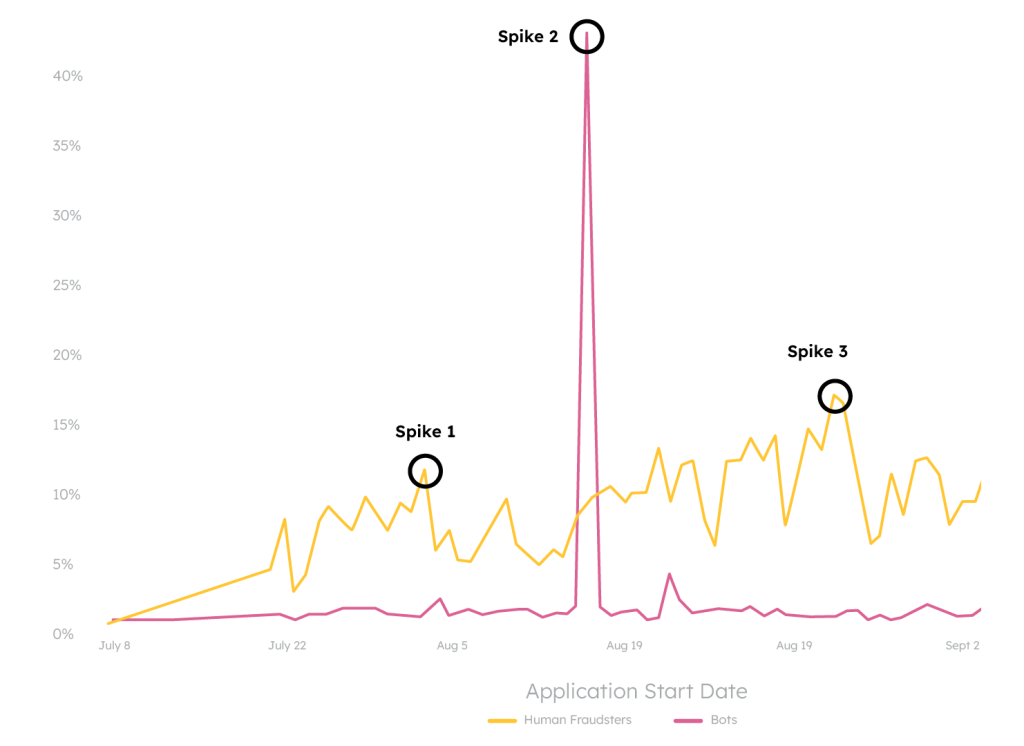
Investigate each spike to reveal fraudsters’ tactics.
This is another prime example of why behavioral analytics is crucial in stopping modern fraud attacks. First, real-time visibility is critical: without it, you might miss the slow-rolling human attack until it’s too late. More importantly, behavioral analytics can stop all of these risky users as they arrive, blocking both human attacks and bot distractions from entering your ecosystem entirely.
The Value of Visibility
Ultimately, “can you spot a hidden fraud attack?” is a loaded question. Can you see the type of visitors at your doorstep? Do you have the right data to separate risky users from genuine before you let them in? And can you differentiate a lone intruder from a coordinated ring?
If your answer to all of these is “no”, then you’re probably playing catch-up to fraud attacks, giving fraudsters a chance to fool you with deceptive strategies or overwhelm you with in-and-out blitzes.
To learn more about these attacks, how to spot them, and the best ways to defend against them, download The Fraud Attack Strategy Guide.


