
The 3 Most Dangerous Fraud Attack Strategies of 2025 (and How to Fight Back)
In 2025, we’re seeing fraud attacks reach a new level of sophistication and intensity. With high-powered GenAI tools at their fingertips, fraudsters are launching attacks that blend automation, human ingenuity, and psychological misdirection to wreak havoc on digital businesses.
These attacks aren’t carried out by hooded individuals hiding in basements. They’re coordinated, military-like efforts that blend advanced tools with sophisticated strategies to bypass even the most advanced defenses. Here are the biggest strategies to look out for, plus the keys to fighting back against them.
Attack #1: The Blitz
At first glance, an all-out, short-lived attack seems straightforward. See the large red spike here, representing an uptick in risky traffic. This example is from a top bank — it’s as if fraudsters picked their target and immediately launched a massive attack.
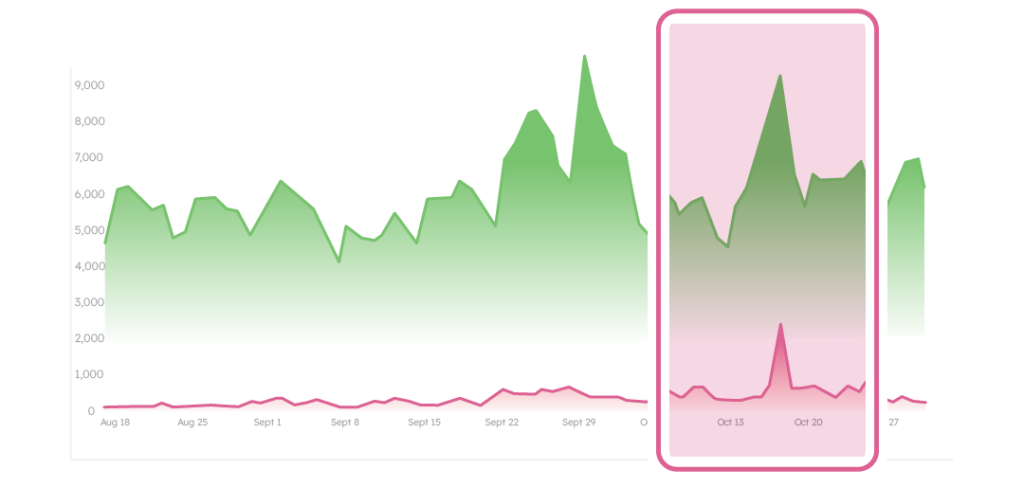
This attack is dangerous because of its scale, but it’s more sophisticated than an in-and-out onslaught. Take a look at what happens before the attack: NeuroID is able to segment the risky traffic, identifying human fraudsters (yellow) and bots (red). With this visibility, we see a tag-team effort taking place. Humans start off by probing the bank’s application, then test a bot script to exploit any vulnerabilities they find. The process repeats until the fraudsters create bots capable of completing the application. Then they deploy their bot armies at full strength.
These brute-force attacks are designed to cripple defenses and overwhelm fraud teams. If you don’t have the right tools in place to see the buildup, blitzes will arrive without warning.
The Counter: Pre-submit visibility
Staying ahead of blitz attacks requires constant visibility into fraudsters’ behavior, particularly insight into fraudsters who aren’t completing an application. If you can only see and stop fraud after it’s been submitted, you’ll miss the extensive testing that fraudsters are carrying out on your application flow — and won’t be able spot a blitz until it’s too late.
Attack #2: The Feint
Here’s another full-force attack — or so it seems. This one is from a lender; here’s a breakdown of traffic on their application.
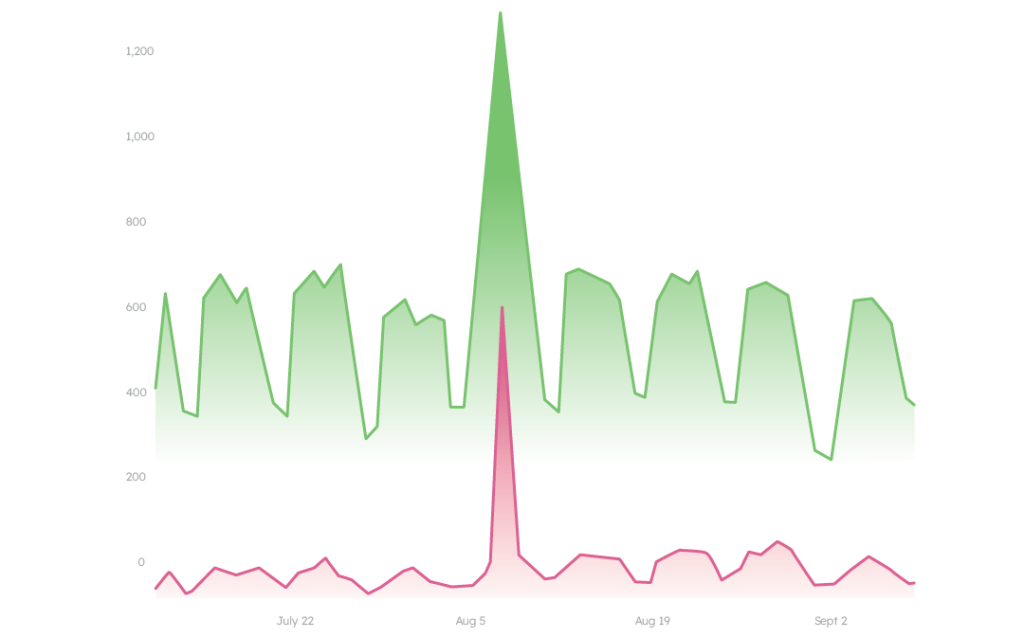
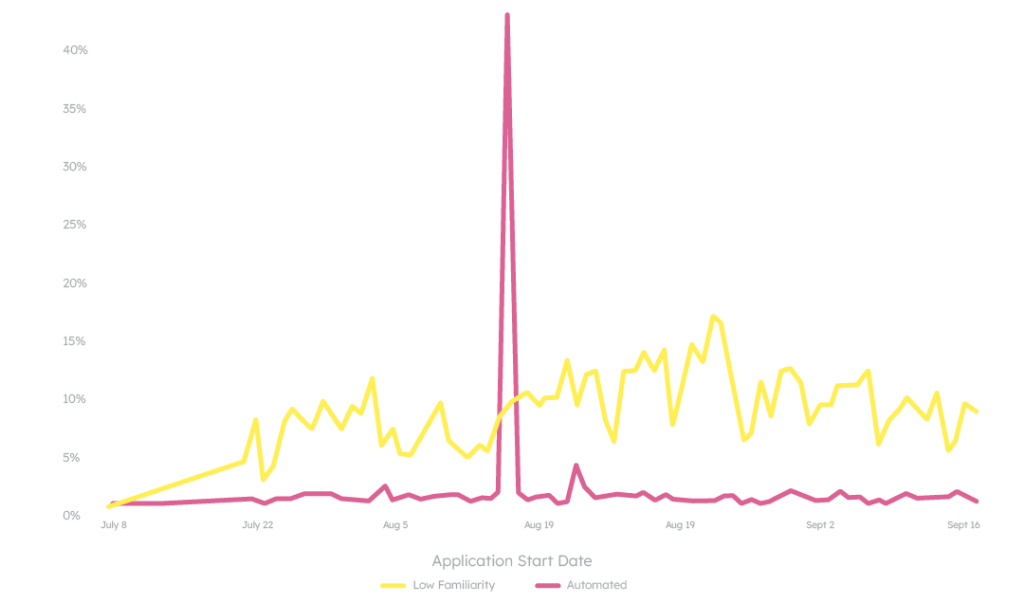
There are two key differences that separate this attack from the last one. First, these fraudsters aren’t trying to hide. In the last attack, despite the spike in risky users, the bank’s total volume never exceeded its baseline. That was by design, an intentional effort not to draw extra attention. This attack, however, is obvious and stands out aggressively.
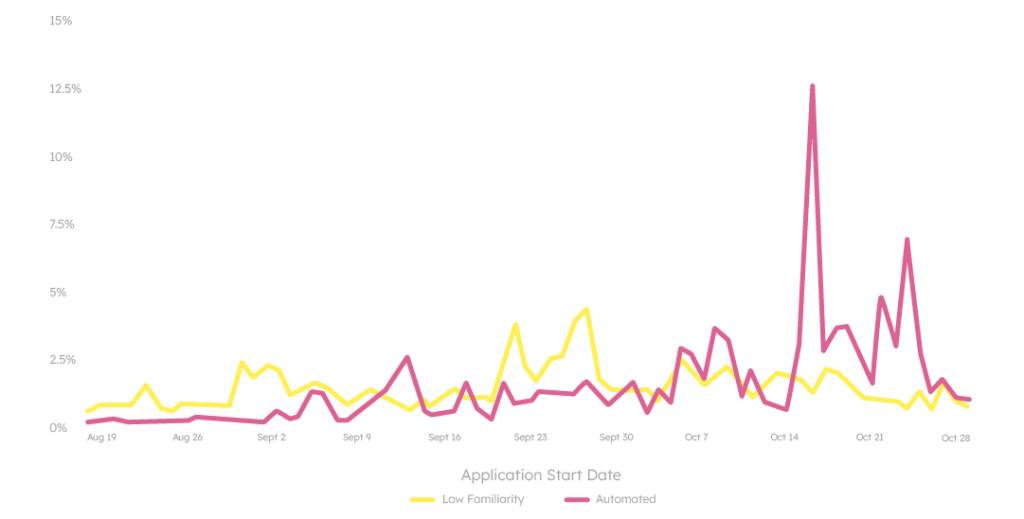
Second, if we segment this risky traffic again between humans and bots, we don’t see the same tag-team testing that typically precedes a spike of this size.
What we do see is a slow-rolling group of human fraudsters that picks up its pace following the large bot spike. The bot spike is nothing but a distraction. It’s designed to draw attention away from the real threat: the underlying human fraudsters.
The Counter: Real-time alerting for all fraud types
If and when your fraud team stops a bot blitz, they probably feel really good — maybe too good — about their defenses. Fraudsters want to exploit that. Underneath the brief fraud uptick may be a long-lasting parasitic attack, hiding in the status quo and continually deferring attention by staging blitz attacks.
If you’re not looking past the surface of attacks for ongoing and underlying trends, you could be missing a much more dangerous threat. Having a tool that provides insight into both human- and bot-led fraud keeps one attack type from overshadowing the other.
Attack #3: Guerrilla Warfare
There’s a commonality in the first two attacks: they both involve humans planning and carrying out attacks over the course of multiple weeks. They’re easy to describe because each step builds on the last. If fraud teams keep an eye out for the early indicators, they can often prepare for the attack before it strikes.
Recently, we’ve seen a change. Not only are fraudsters relying more on bots to identify vulnerabilities in their targets’ fraud stacks, but the testing and attacks are happening simultaneously. Bots are entering an application and appearing to adapt on the fly. In one attack on a BNPL provider’s loan application, we saw five distinct bot clusters form, each finding new vulnerabilities as they progressed through the loan application (this is a fascinating but long story; check out our latest report for the full breakdown).
The Counter: Modern, adaptive fraud detection solutions
Fraudsters are evolving and constantly finding new ways to beat your defenses. If you put a static, one-size-fits-all fraud stack in front of them, they’ll use their advanced tools to find their way through it in no time. Solutions to stop today’s fraudsters need to be as agile as the attacks they’re facing.
Fighting Back Against Fraudsters
Fraudsters are only growing smarter, savvier, and more strategic. Defending against them demands an equally sophisticated fraud stack can keep your business a step ahead.
For a deeper dive into fraudster tactics — and how experts are fighting back — download The Fraud Attack Strategy Guide.



