Blog
Read More
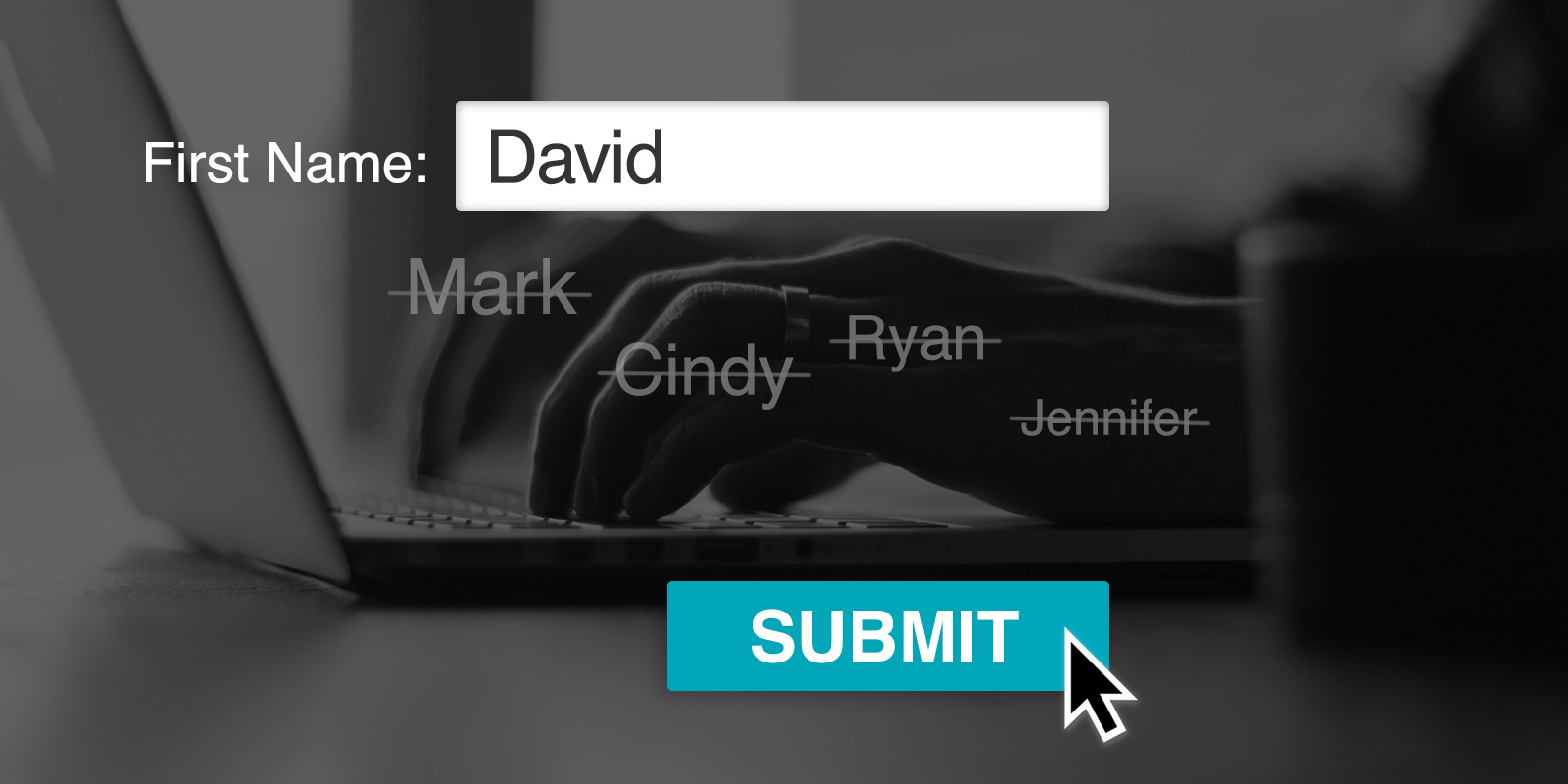
Spot the imposter: Comparing high-risk login attempts
Fraudsters are becoming experts at mimicking genuine users, making even routine‑looking login attempts potential gateways for coordinated account‑takeover attacks. This blog walks through real‑world scenarios to reveal the subtle behavioral signals that distinguish imposters from trusted customers—and how those signals can strengthen your defense strategy.