Spot the imposter: Comparing high-risk login attempts
In an account takeover (ATO) attempt, fraudsters don’t kick down the door. Instead, they disguise themselves as genuine users and act as imposters, fooling defenses into giving them access to accounts that don’t belong to them.
Today, these efforts are highly coordinated and methodical. Fraud rings and individual fraudsters alike follow step-by-step playbooks that tell them exactly how to blend in. As a result, seemingly routine login attempts are often the key cogs in larger, orchestrated ATO efforts. And while MFA or other forms of step-up authentication catch the obvious outliers, they struggle to stop well‑prepared, well-equipped attackers.
Let’s put your instincts — and your ATO prevention strategy — to the test. For each scenario, you’ll get a snapshot of a login attempt: device behavior, authentication patterns, and the small but telling signals that reveal intent. Your mission? Keep the fraudsters out, without causing headaches for your legitimate customers.
Login 1
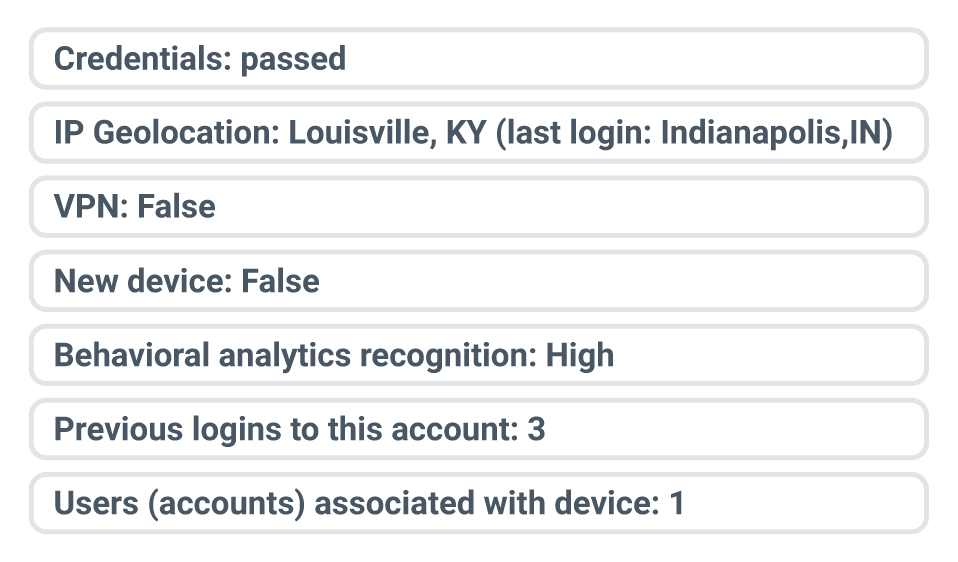
Approve, step up or block this login.
Login 2
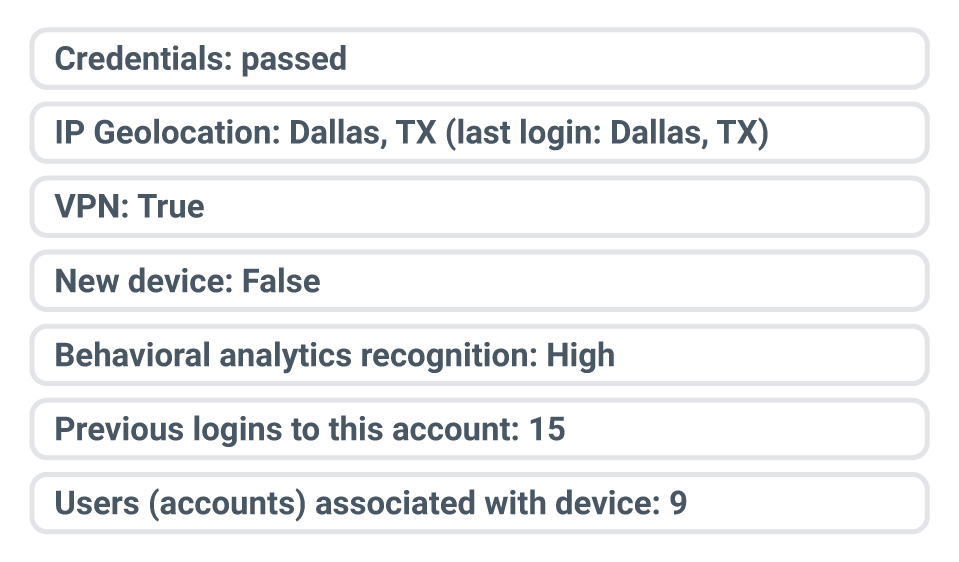
Approve, step up or block this login.
Login 3
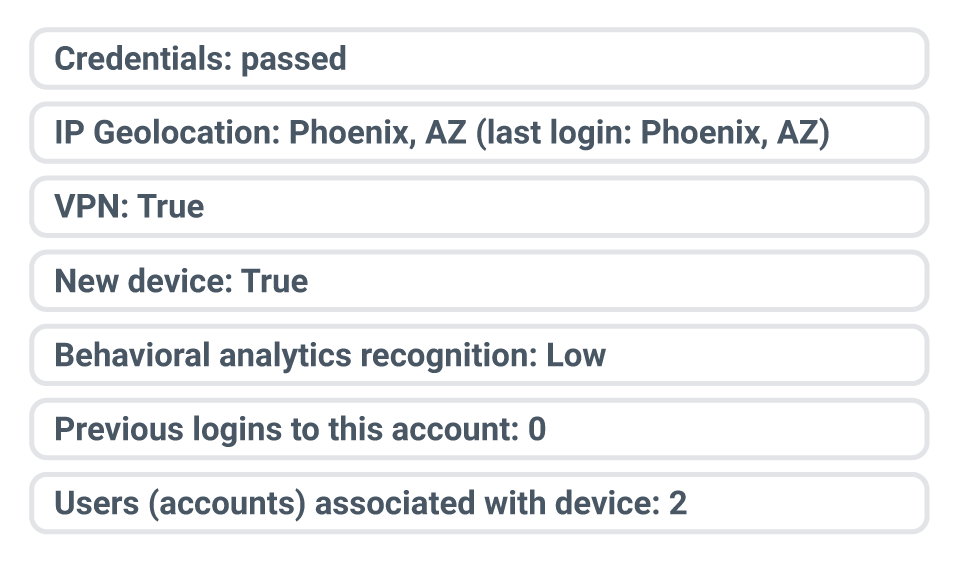
Approve, step up or block this login.
If these scenarios felt ambiguous, that’s the point. Fraudsters thrive in the gray areas, disguising themselves well enough to make fraud teams hesitate to lock them out. What you see here is only a slice of the picture; NeuroID’s signals uncover the fuller story: device linkage, behavioral patterns and coordinated activity that reveal ATO attempts — and allow us to stop them in real time.
Want to see how fraudsters’ ATO strategies look in a real-world example? Check out our latest report — and see how NeuroID exposed and stopped a fraud ring’s ATO attack in action.