How Behavior Works: A Login Workflow Comparison
Earlier this year, I covered the role of behavioral analytics in onboarding flows: reducing fraud, streamlining workflows and improving conversion at account opening. But the use cases extend beyond there.
Account takeover and other types of fraud that occur at login present a unique set of challenges for businesses and are a critical point of vulnerability and friction. Luckily, just like onboarding, behavioral analytics can transform these flows into seamless, secure experiences.
Let’s walk through a traditional login workflow, then compare it to one with behavioral analytics to see how behavior-based decisioning changes everything.
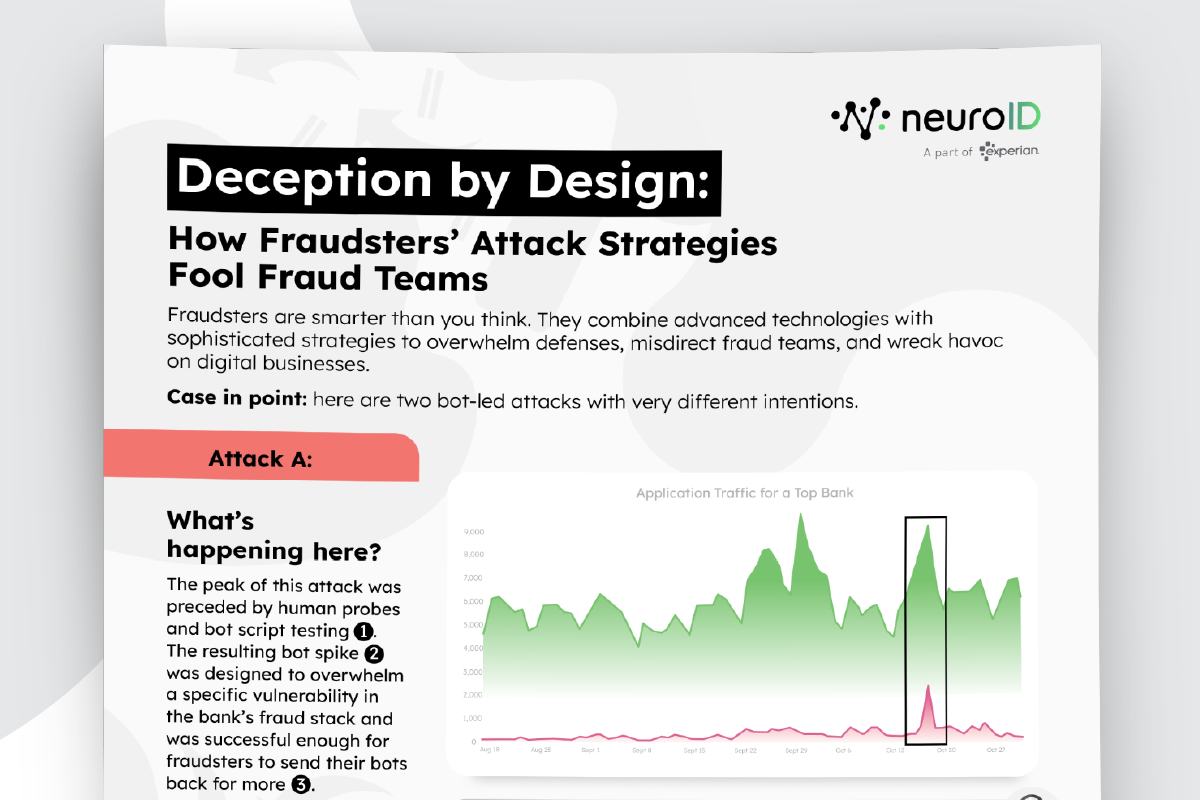
Login Without Behavioral Analytics
In this standard login flow, the user arrives at the login page and enters their credentials. From there, they’re routed through an additional authentication method — often a PIN, OTP, push notification, biometric, or security question.
This approach has a few major drawbacks:
- No early risk signal: Assuming the user’s credentials are correct, you’re flying blind until the user hits an authentication step.
- Friction for everyone: Legitimate users face the same hurdles as fraudsters.
- Reactive decisioning: You’re responding to threats after they’ve already entered your ecosystem.
Most of all, you’re relying heavily on the user’s credentials and hoping they haven’t been compromised and placed in the hands of a fraudster. To compensate, genuine users are forced through the same series of friction-filled fraud checks — and may drop off if, say, they don’t have access to their MFA method or can’t remember answers to their security questions. And still, fraudsters with stolen credentials and spoofed devices will often slip past these checks and remain undetected.
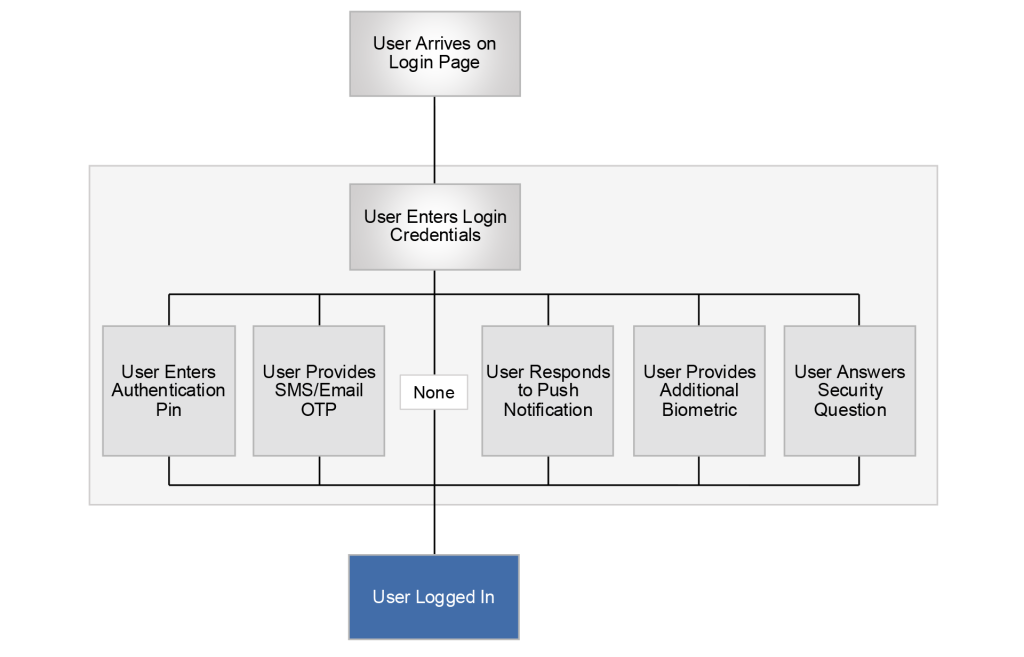
Login With Behavioral Analytics
Now let’s add behavioral analytics to the mix. In this flow, NeuroID starts collecting behavioral, device and network data as soon as the user arrives on the login page, before any information is entered. In real-time, behavioral analytics detects both human fraudsters and bots based on how they’re interacting with the website or app session, not just their credentials.
In this scenario, the behavioral analytics API is called after the user enters their login credentials. Now, users are funneled dynamically based on their intent:
- Proactive fraud prevention: High-risk logins are prevented before fraudsters can access the accounts.
- Frictionless for good users: Legitimate users bypass strenuous authentication.
- Efficient resource use: Top-of-funnel fraud capture reduces pressure (and spending) on downstream tools and manual reviews.
This flow is smarter, faster, and safer:
- High-risk users are blocked immediately, preventing account takeover attempts in real-time.
- Medium-risk users are directed to the same series of step-ups that every user was forced through without behavioral analytics.
- Low-risk users get a streamlined experience, logging in without additional checks.
Unlike the first flow, this one adds no additional friction for genuine users and provides an additional layer of protection against sophisticated account takeover schemes, scams, bot attacks, and more.
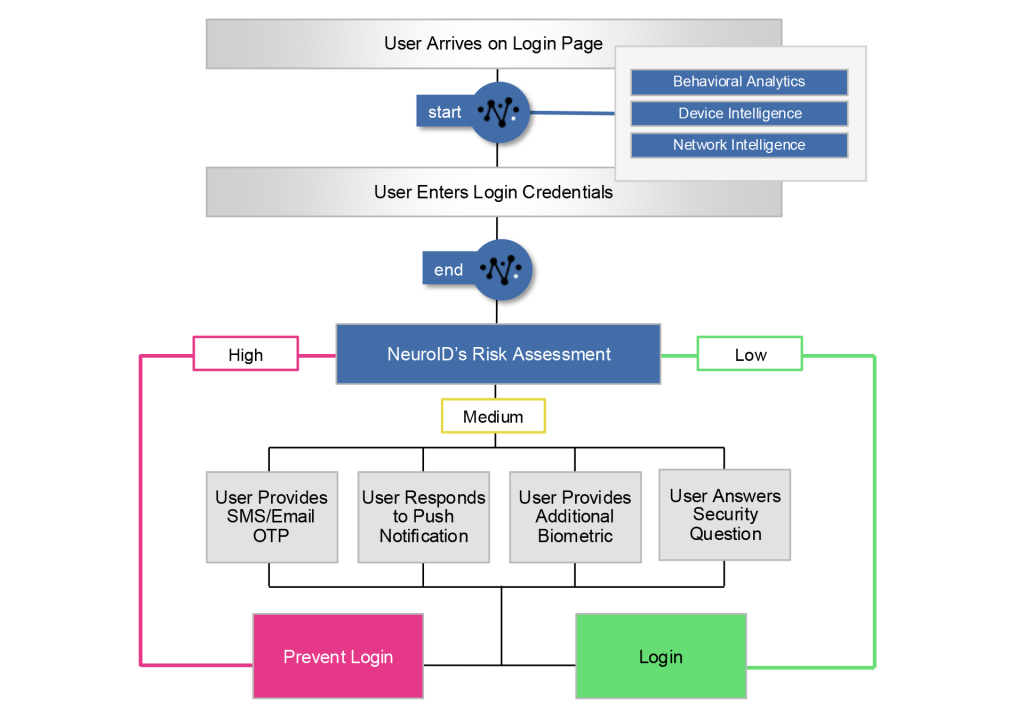
Alternative Approach: Detect Now, Decision Later
In the above scenario, a risky login attempt would be blocked before it could go any further. But some companies I speak with are understandably hesitant to block a user simply trying to log in — they don’t want to deny anyone until they have to.
These companies take a different approach. They delay calling the behavioral analytics API until the user attempts a higher-risk activity. So, even if red flags are flying during the login session, that user can access the account. But when they go to view sensitive data, change profile information, or complete a transaction, that’s when action is taken.
The flow above shows what it looks like to decision at profile changes. The user is already logged in, then attempts to change information on the profile (maybe a shipping address, phone number, or payment method). Using all the data we’ve gathered up to this point (including the login session), NeuroID provides a decision about this user’s intention that determines if the changes should be saved or declined. This approach still gets the job done: fraudsters are stopped before damage occurs, and genuine users aren’t burdened with additional authentication methods.
Behavioral Analytics: A Top-of-Funnel Game Changer
Whether it’s at onboarding, login, or transaction behavioral analytics shines as a first line of defense against third-party threats of all kinds. It gives you a real-time read on user intent, enabling smarter decisions across the entire fraud stack. Combined with device and network intelligence, you get a multi-layered defense that enables better user experiences while effectively stopping sophisticated fraudsters.
Ready to bring behavioral analytics into your login flow? Start with our 2025 Buyer’s Guide to Behavioral Analytics for Fraud Prevention, then view an interactive demo to see behavior in action.